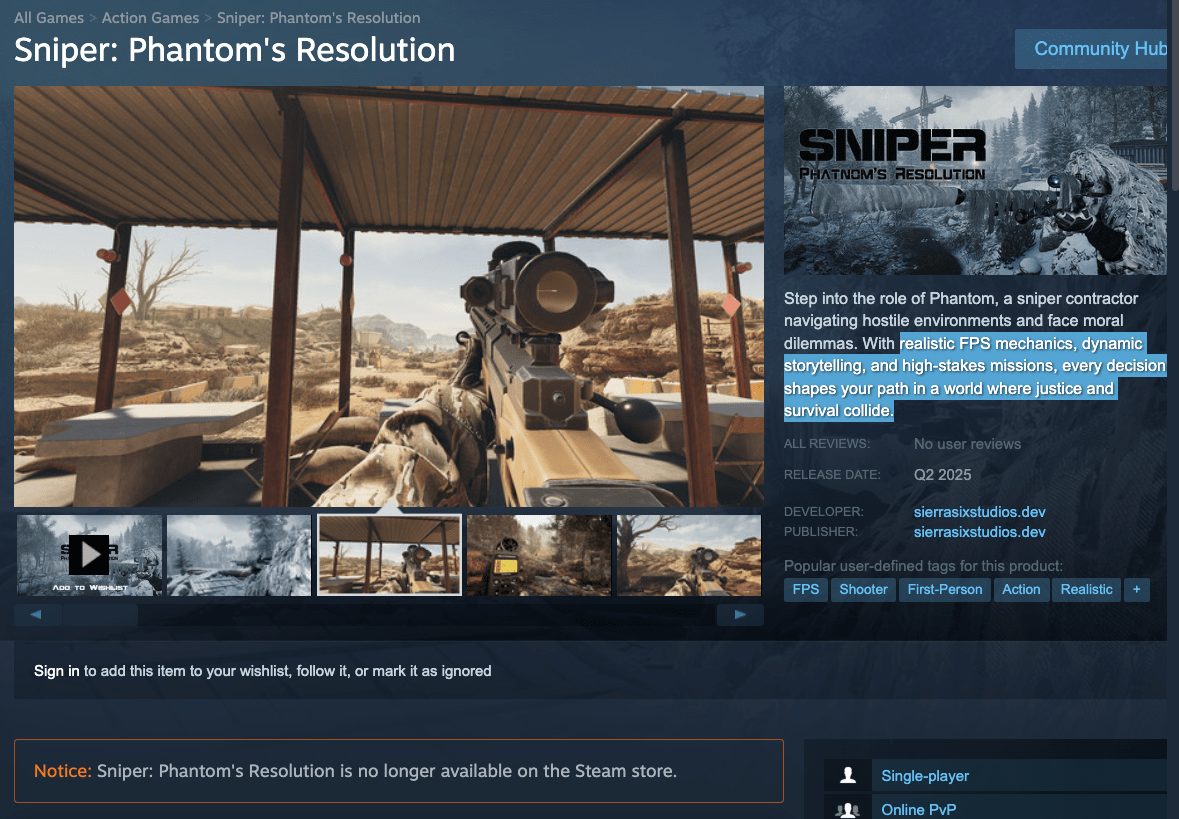
Valve Removes Video Game Demo Suspected of Being Malware
Valve removed a video game from its online store steam after users reported that a free demo for the game was installing malware on their computers. The game was called sniper: Phantom’s resolution, and promised to give players “realistic [first-person shooter] Mechanics, dynamic storytelling, and high-stakes missions, “According to an archive of its steam page, … Read more